Hi,
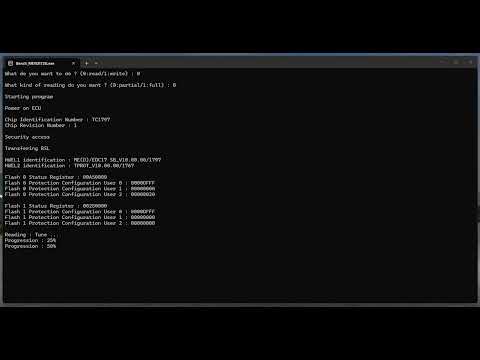
I try to do a bootstrap loader on my Bosch MEVD17.2.G (TC1797 mcu) in bench mode without opening the ecu as my PCMflash tool does but I am stuck at the security access before transfering the bootloader. I think it is a sort of seed key : ecu sends 10 kind of random bytes and the host must answer with 20 bytes. I was sure the algorithm was in the BootRom (0x8FFFC000-0x8FFFFFFF) but after successfully dumped and disassembled it I haven’t found the algorithm in the code (only 16kb). Maybe someone know where is located this algorithm in the code ?
I try to do a bootstrap loader on my Bosch MEVD17.2.G (TC1797 mcu) in bench mode without opening the ecu as my PCMflash tool does but I am stuck at the security access before transfering the bootloader. I think it is a sort of seed key : ecu sends 10 kind of random bytes and the host must answer with 20 bytes. I was sure the algorithm was in the BootRom (0x8FFFC000-0x8FFFFFFF) but after successfully dumped and disassembled it I haven’t found the algorithm in the code (only 16kb). Maybe someone know where is located this algorithm in the code ?


Comment